How Symmetric Encryption Secures PHP Scripts
Symmetric encryption protects PHP scripts by using a single key for both encrypting and decrypting data. This approach ensures sensitive information like database records, cookies, and files remains secure. Modern PHP tools like Libsodium and OpenSSL simplify encryption by providing built-in features for data integrity and security. Additionally, tools like SourceGuardian protect PHP code by converting it into encrypted bytecode, preventing unauthorized access or tampering.
Key points to know:
- Libsodium (bundled since PHP 7.2) offers secure encryption with minimal configuration.
- OpenSSL supports AES-GCM for authenticated encryption but requires more manual setup.
- SourceGuardian encrypts PHP scripts and locks them to specific domains or servers, ensuring tighter security.
Symmetric Encryption Basics in PHP
Keys, IVs, and Nonces
An encryption key is the secret ingredient that locks and unlocks your data. In PHP, you can generate secure keys using a Cryptographically Secure Pseudo-Random Number Generator (CSPRNG) like random_bytes() or sodium_crypto_aead_xchacha20poly1305_ietf_keygen().
An Initialization Vector (IV) is what ensures that even if the same data is encrypted multiple times, the resulting ciphertext looks different each time. This prevents patterns from being revealed in block ciphers like AES-CBC. While an IV doesn’t need to be kept secret, it must be unique for each encryption operation.
Nonces (short for “numbers used onceâ€) are used with stream ciphers or AEAD (Authenticated Encryption with Associated Data) modes such as GCM. As PHP.Watch explains:
A nonce does not necessarily have to be random, but it must be unique.
The rule is simple: never reuse a nonce with the same encryption key.
Recommended Algorithms and Modes
For new PHP projects, XChaCha20-Poly1305 is a top choice. It uses a 192-bit nonce and includes built-in authentication, which removes concerns about nonce collisions. Another excellent option is AES-256-GCM, especially if your system supports hardware acceleration via AES-NI. This mode provides authenticated encryption, meaning it automatically protects against tampering.
If you’re using older OpenSSL modes like AES-256-CBC or AES-256-CTR, you’ll need to manually add authentication using HMAC-SHA256. As Paragon Initiative Enterprises points out:
Encryption without message authentication is NOT secure.
Fortunately, the Sodium extension, which has been bundled with PHP since version 7.2, simplifies the process by offering authenticated encryption out of the box.
Common Mistakes to Avoid
Some pitfalls can seriously undermine encryption security. For starters, avoid using ECB mode. As PHP.Watch warns:
From the outset, AES modes such as ECB (Electronic codebook) are not semantically secure.
ECB mode creates identical ciphertext blocks for identical plaintext, exposing patterns and making it unsuitable for most use cases.
Another mistake is relying on the outdated mcrypt extension, which was removed in PHP 7.2 and is no longer supported. Reusing nonces or IVs with the same key is another critical error, particularly with stream ciphers, as it compromises the integrity of your encryption.
Hardcoding encryption keys in your source code or committing them to version control is a glaring vulnerability. And when verifying Message Authentication Codes (MACs), always use hash_equals() instead of standard comparison operators to avoid timing attacks.
Up next, we’ll dive into configuring your PHP environment to put these encryption practices into action effectively.
Encrypt and Decrypt Data Securely in PHP: OpenSSL, Sodium & defuse/php-encryption
Setting Up Your PHP Environment
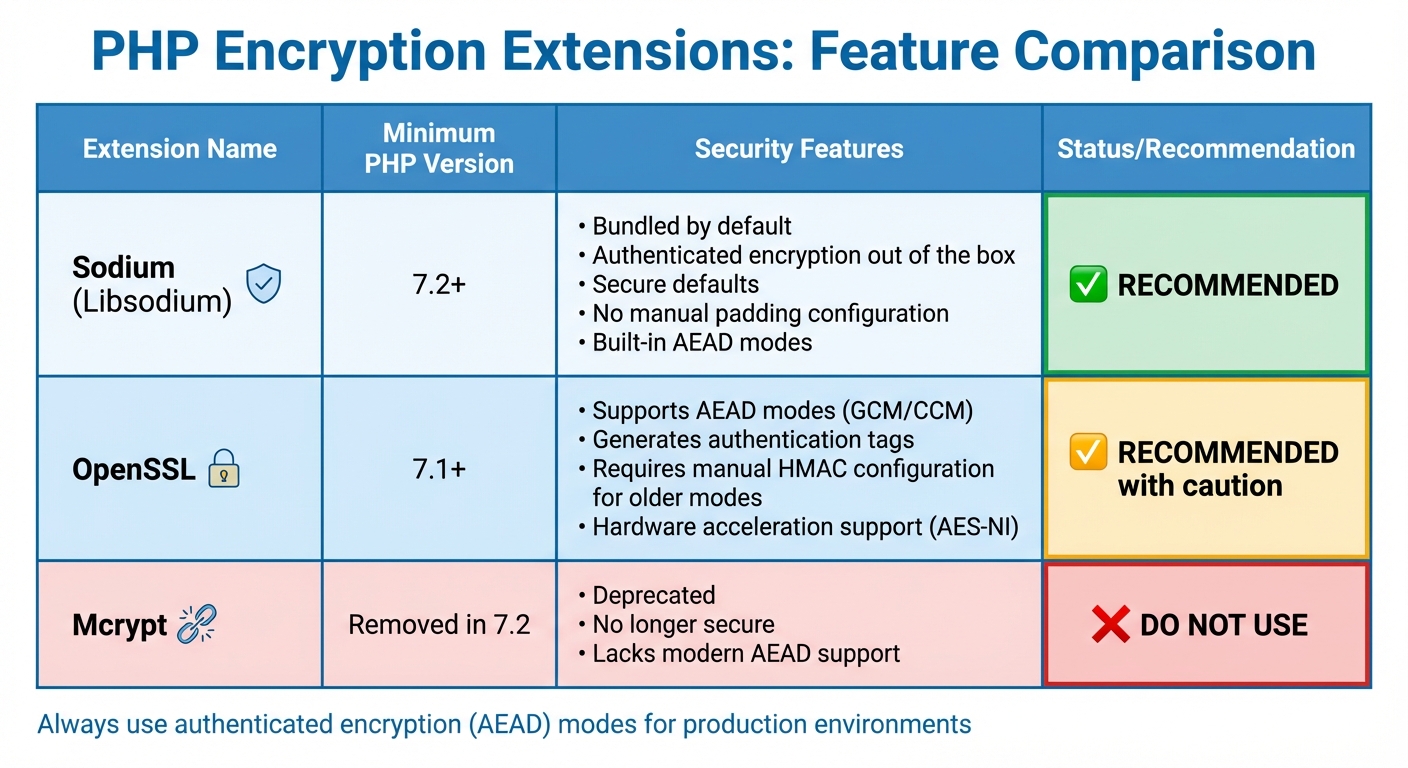
PHP Encryption Extensions Comparison: Sodium vs OpenSSL vs Mcrypt
PHP Extensions and Version Requirements
To ensure a secure and functional PHP environment, confirm that your setup includes the necessary extensions. Starting with PHP 7.2, the Sodium extension (Libsodium) is bundled with PHP by default. Sodium simplifies encryption by offering authenticated encryption out of the box, eliminating the need for manual HMAC configuration.
If you're using OpenSSL, make sure you're running PHP 7.1.0 or newer. This version introduces support for AEAD modes like GCM and CCM, which generate authentication tags for added security. Older PHP versions lack the $tag parameter required for these secure modes. Using AES without authentication, such as in CBC mode, can expose your application to padding oracle attacks.
To confirm the availability of extensions, you can run the following command:
php -m | grep sodium
Alternatively, you can check the output of phpinfo(). Avoid using mcrypt, as it was removed in PHP 7.2 and is no longer secure.
| Extension | Minimum PHP Version | Security Features |
|---|---|---|
| Sodium | 7.2+ | Secure defaults; no manual padding configuration |
| OpenSSL | 7.1+ | Requires AEAD modes (GCM/CCM) for authentication tags |
| Mcrypt | Removed in 7.2 | Deprecated and insecure - do not use |
These extensions are essential for safe encryption practices.
Secure Key Storage Methods
Never hardcode encryption keys directly into your PHP scripts. Since PHP is interpreted, embedding keys makes them vulnerable to exposure. Instead, use environment variables or a secrets management solution to store keys securely.
For generating secure encryption keys, use functions like random_bytes() or \Sodium\randombytes_buf(). Symfony’s documentation highlights the importance of protecting sensitive files:
The
prod.decrypt.private.phpfile is highly sensitive. Your team of developers and even Continuous Integration services don't need that key.
For production environments, deploy keys securely using files or base64-encoded environment variables, such as SYMFONY_DECRYPTION_SECRET. If a key is compromised - for example, due to an employee leaving the organization - immediately rotate the key and re-encrypt all data with the new key.
Next, we’ll explore how you can protect your PHP scripts themselves with SourceGuardian.
Using SourceGuardian for Script Protection
While encryption secures your data, SourceGuardian adds an extra layer of protection by safeguarding your PHP scripts. It compiles PHP code into binary bytecode and layers it with encryption, preventing unauthorized access or tampering.
No changes can be made to the protected scripts once they have been encoded... any changes to an encoded file will make it unusable.
SourceGuardian supports PHP versions from 4.x to 8.5, making it compatible with a wide range of setups. It also allows you to lock scripts to specific environments, such as a particular IP address, domain name, or hardware MAC address. This is especially useful for production servers with fixed infrastructure.
To run protected scripts, you’ll need to install the free SourceGuardian Loader extension on your server. Use the online Loader Assistant to identify the correct loader version based on your operating system, CPU architecture, and PHP thread-safety configuration. Pricing starts at $249.00 for the Standard license, while the PRO version, which includes CI/CD integration for automated deployments, costs $399.00.
sbb-itb-f54f501
How to Implement Symmetric Encryption in PHP
Once your PHP environment is securely configured, you can implement encryption using OpenSSL or Libsodium.
Encrypting with OpenSSL
The openssl_encrypt() function is a key tool for symmetric encryption in PHP. If you're running PHP 7.1 or later, using AES-256-GCM is highly recommended. This mode not only encrypts your data but also provides integrity verification with an authentication tag.
Here's how to get started:
- Generate a 32-byte encryption key: Use
random_bytes(32)for AES-256. - Create a unique Initialization Vector (IV): Use
random_bytes(openssl_cipher_iv_length('aes-256-gcm')). - Encrypt your data: Pass the encryption key, IV, and data to
openssl_encrypt(). For AEAD modes like GCM, ensure you pass the authentication tag parameter by reference to verify data integrity during decryption.
If you’re using AES-256, make sure your key is exactly 32 bytes long. When using CBC mode instead of GCM, you’ll need to manually implement integrity checks. Use hash_hmac() to create a MAC (Message Authentication Code), and verify it with hash_equals() to guard against timing attacks.
Encrypting with Libsodium
Libsodium offers a simpler and more secure approach to encryption. Starting with PHP 7.2, Libsodium is bundled by default, making it easy to use secure encryption algorithms with authenticated encryption built-in.
Here’s how to encrypt with Libsodium:
- Generate a secret key: Use
sodium_crypto_secretbox_keygen()for the XSalsa20-Poly1305 algorithm. - Create a unique nonce: Generate it with
random_bytes(SODIUM_CRYPTO_SECRETBOX_NONCEBYTES). Nonces don’t need to be secret, so you can store them alongside the ciphertext. - Encrypt your data: Use
sodium_crypto_secretbox($message, $nonce, $key). - Decrypt your data: Use
sodium_crypto_secretbox_open($ciphertext, $nonce, $key). If the data has been tampered with, this function will returnfalse.
For added security, clear sensitive data from memory using sodium_memzero(). Libsodium is designed to resist side-channel attacks, which can uncover secret keys in milliseconds. To convert keys or data to hex or base64, always use Sodium's timing-safe functions like sodium_bin2hex() to avoid leaking information.
These techniques are not limited to encrypting messages - they’re also effective for securing data stored in databases or files.
Encrypting Databases and Files
When encrypting database fields, assign each record a unique IV or nonce and store it in a separate column alongside the ciphertext. To enable searching over encrypted fields without decrypting every row, use a blind index. A blind index is a separate column containing a keyed HMAC hash of the plaintext. Always use a different key for the blind index to minimize risk if one key is compromised.
For large files, encrypt them in chunks (e.g., 16 KB) to avoid memory issues. Protect configuration files and other non-PHP assets by encoding them with tools like SourceGuardian, ensuring decryption is only possible through protected scripts.
To maintain both confidentiality and integrity, always use AEAD modes such as AES-GCM or ChaCha20-Poly1305. As Paragon Initiative Enterprises emphasizes:
Encryption without message authentication is NOT secure.
Finally, store your encryption keys securely - use environment variables or files outside the web root. Never commit keys to version control systems. This step is critical to safeguarding your encrypted data.
Securing PHP Scripts in Production
Access Control and Key Management
When deploying PHP scripts in production, it's critical to enforce strict access controls for encryption keys and other sensitive data. Keys should be stored securely, such as in environment variables configured at the server level (e.g., using Apache's SetEnv directive) or in configuration files placed outside the web root.
For added security, consider using envelope encryption. This method involves encrypting data with a Data Encryption Key (DEK), which is then wrapped by a Key Encryption Key (KEK) managed by services like Google Cloud KMS or AWS KMS. If your server is compromised, you can immediately revoke API access to the KEK, effectively cutting off an attacker's ability to decrypt stolen data. As Ashley Simpson from Delicious Brains explains:
The KMS API access can be revoked, thus preventing an attacker from decrypting any data they've made off with. With regular secret key encryption where a single local key is compromised, you don't have that luxury.
It's also important to follow the principle of least privilege. Grant your web server only the permissions it absolutely needs to access key files or KMS APIs. Additionally, implement a key rotation strategy to minimize the risk of long-term exposure.
Key Rotation and Legacy Data
Rotating encryption and authentication keys every 90 days is a best practice. As timoh6 points out:
rotating keys by some period of time might cut [an adversary's] access... This may make the damage smaller because the adversary can not abuse the leaked keys endlessly.
To manage this process, include a key version identifier with your encrypted data. This allows you to reference the correct historical key when decrypting. Keep older keys in a "retired" state until all data encrypted with them has been migrated to the new key.
For large datasets, envelope encryption is especially useful. You can rotate the KEK without re-encrypting all your data. The DEK remains valid for existing records, while the new KEK is used to wrap future DEKs. Legacy data can still be decrypted with the old KEK until the migration is fully completed.
Advanced Protection with SourceGuardian
In addition to securing data, protecting your PHP scripts themselves is equally important. SourceGuardian offers a robust solution by converting your PHP code into encrypted binary bytecode. This ensures scripts can only run on authorized domains, IP addresses, or machines. For example, domain locking integrates the domain name into the encryption key, making it impossible to execute scripts on unauthorized domains. Additional restrictions, like IP, MAC, or Machine ID locking, provide further layers of security.
SourceGuardian also includes a built-in License Generator, enabling you to create external license files with custom locking options for each customer. To prevent file substitution attacks, it enforces project-wide protection, ensuring all scripts in a project work only when used together. Even non-PHP files, such as HTML templates, are encoded to ensure they can only be decrypted by scripts within the same protected project.
With support for PHP versions from 4.x to 8.4 and compatibility across platforms like Windows, Linux, macOS, and FreeBSD, SourceGuardian integrates smoothly into modern CI/CD workflows. The PRO version, launched in May 2024, adds even more functionality for secure development.
Conclusion
As we've explored encryption basics, environment setup, and implementation, it's clear that layering protection is essential for securing your PHP applications.
While symmetric encryption effectively safeguards sensitive data like records, credentials, and files, it doesn't protect your business logic. Tools such as Libsodium and OpenSSL handle data protection, but encryption routines and key management can still be weak points.
This is why combining data encryption with script protection is critical. Data encryption ensures your information remains confidential and intact, using authenticated encryption (AEAD). At the same time, tools like SourceGuardian protect your code by securing intellectual property.
Even in the event of a server breach, multiple layers of defense remain intact. Encryption keys are securely managed, and scripts are locked to specific domains, IP addresses, or hardware identifiers. SourceGuardian adds another layer by decrypting bytecode only during execution and re-obfuscating it immediately, preventing memory dumps.
These strategies work together to create a strong shield against unauthorized access.
Key Takeaways
-
Rely on Libsodium for Data Encryption:
Since PHP 7.2, Libsodium has been included as a built-in library, offering secure, authenticated encryption. Functions likesodium_crypto_aead_xchacha20poly1305_ietf_encrypt()provide robust protection. For older OpenSSL modes, always follow an encrypt-then-MAC approach, and never hardcode encryption keys into your application. -
Use SourceGuardian for Code Security:
SourceGuardian's domain locking feature ties the encryption key to specific servers, ensuring scripts only run in authorized environments. With compatibility for PHP 8.5 and CI/CD integrations in its PRO version, it fits seamlessly into modern workflows. As Alexander Heuts from Blue Moon IT shares:
We're delighted with SourceGuardian. It gives us all we need to protect our investments.
FAQs
How does SourceGuardian protect PHP scripts from unauthorized access?
SourceGuardian strengthens the protection of PHP scripts by transforming source code into binary bytecode. This process makes the code unreadable and much harder to reverse-engineer. On top of that, it uses encryption and obfuscation to provide an added shield of security.
Beyond basic protection, SourceGuardian includes advanced features like IP, domain, or hardware locking, time-based licenses, and dynamic licensing capabilities. These tools ensure your scripts run only in approved environments, effectively preventing unauthorized access or distribution.
Why choose Libsodium over OpenSSL for encrypting PHP scripts?
Libsodium is a cutting-edge cryptography library integrated directly into PHP as a core extension, offering a secure and user-friendly approach to encryption. It simplifies encryption tasks with a streamlined API and secure defaults, such as built-in nonce management and authenticated encryption, which help minimize the chances of misconfiguration.
When compared to OpenSSL, Libsodium shines for its simplicity, protection against side-channel attacks, and use of modern, thoroughly vetted algorithms like ChaCha20 and Poly1305. It's also built for speed and portability, frequently outperforming similar OpenSSL implementations without relying on external dependencies. These qualities make Libsodium an excellent choice for securing PHP scripts efficiently and reliably.
Why is it risky to reuse nonces or initialization vectors (IVs) with the same encryption key?
Reusing nonces or initialization vectors (IVs) with the same encryption key can weaken the security of your encrypted data. These elements are designed to make sure each encryption process generates a distinct ciphertext, even if the same plaintext is encrypted repeatedly. When nonces or IVs are reused, attackers might detect patterns or links between encrypted messages, putting sensitive information at risk.
To keep your encryption robust, always generate unique nonces or IVs for every encryption process. This is particularly important in symmetric encryption, where the same key handles both encryption and decryption. Managing nonces and IVs correctly is a key part of safeguarding your PHP scripts and protecting sensitive data.


